If your web application is running under ApplicationPoolIdentity account, you must have had the headache of configuring permission to this account. The trick of using IIS APPPOOL\Name has never worked for me. In order to find this user in the permission configuration window, I have been running ICACLS commend every time. This post has more detail on both approaches.
Now if your ApplicationPoolIdentity-using-web-application utilizes some certificate to encrypt/decrypt messages, such as a WCF web service with message level security based on certificate, you would have to figure out how to assign permission on this certificate to your ApplicationPoolIdentity user.
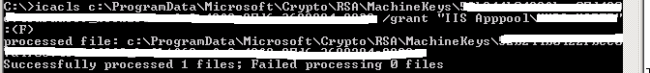
It is actually similar with assigning permission to some other file in that way that you can either use the IIS APPPOOL\Name method or using ICACLS command as described in the post mentioned above. However, if the IIS APPPOOL\Name approach does not work for you, ICACLS approach requires a file path in order to add this user account. The cert is usually stored somewhere deep and is under a different name than your original cert, which makes it difficult to be found.
HOW TO FIND THE PATH TO THE CERT?
First you need a tool called FindPrivateKey.exe from Microsoft. It is funny because you can’t find a download link directly for this executable. It is actually a part of a sample code solution for WCF services. Here is the link to the source codes. Unzip it and compile the project from the folder C:\WF_WCF_Samples\WCF\Setup\FindPrivateKey\. After the compilation, you will have the executable!
This tool can help you find the actual file location of you cert with the cert’s Thumbprint. To find the thumbprint, open Microsoft Management Console.
Add the Certificates snap-in
You should be able to find your cert somewhere
Right click it, select Open. Click on the Details tab in the Certificate dialog. You should be able to find the Thumbprint of your cert.
Now with the thumbprint, run the following command in command line prompt. Note that in the example, I tried to retrieve the cert’s for the local machine. See this page for more details on this tool.
>FindPrivateKey my localmachine -t ” THUMBPRINT “
It will return the folder and name of your cert!
Now a simple ICACLS command can grant the permission needed to our cert.